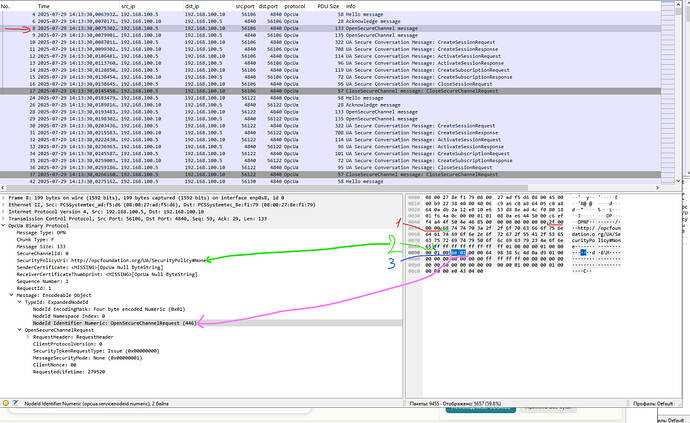
Hi everybody. frame 8. I need to find |be 01| this is the OpenSecureChanel ID, namely 446.
“SecurityPolicyUri” is shown in green at number 2. These data have different lengths. they can reach up to 4096 bytes. There are 4 bytes(red light (1)) in front of “SecurityPolicyUri”, which indicate the length of “SecurityPolicyUri”. Since the length is constantly changing, I need to skip this number of bytes. + after “SecurityPolicyUri” skip 18 bytes (blue) and find the sequence |be 01|.|be 01| in hexadecimal format -Decimal: 48641 (big-endian)|01 be| in hexadecimal form - In decimal system: 446 (little-endian)
I wrote this rule:alert tcp any any → any any (msg:“OPCUa TEST”; flow:established,to_server;
byte_extract:4,12,len_of_policy_uri,little; byte_jump:len_of_policy_uri,16,from_beginning,little,string,dec,post_offset 18; content:“|be 01|”; sid:7000452; rev:8;)This rule no alert. It is written correctly, there is no mistake in it.
I wanted to extract 4 bytes at shift 12 and put it in a variable. BUT I need it in little-endian, and in big-endian traffic. Made byte_extract:byte_extract:4,12,len_of_policy_uri,little;next byte jump:byte_jump:len_of_policy_uri,16,from_beginning,little,string,dec,post_offset 18;I also left little endian, and so that the len_of_policy_uri variable is counted in decimal. But it doesn’t work!
I can’t figure out if I’m putting the endians correctly or if everything counts correctly.
HELP ME, PLEASE
tcp payload:
0000 4f 50 4e 46 85 00 00 00 00 00 00 00 2f 00 00 00 OPNF···· ····/···
0010 68 74 74 70 3a 2f 2f 6f 70 63 66 6f 75 6e 64 61 http://o pcfounda
0020 74 69 6f 6e 2e 6f 72 67 2f 55 41 2f 53 65 63 75 tion.org /UA/Secu
0030 72 69 74 79 50 6f 6c 69 63 79 23 4e 6f 6e 65 ff rityPoli cy#None·
0040 ff ff ff ff ff ff ff 01 00 00 00 01 00 00 00 01 ········ ········
0050 00 be 01 00 00 64 98 38 5c 4d 0a d9 01 00 00 00 ·····d·8 \M······
0060 00 00 00 00 00 ff ff ff ff 00 00 00 00 00 00 00 ········ ········
0070 00 00 00 00 00 00 00 00 01 00 00 00 01 00 00 00 ········ ········
0080 00 e0 43 04 00 ··C··